Category: Technology
Sep 04, 2022 Technology
How Can You Safeguard Your Internet Business Sites?
SSL testaments for secure attachment interface methods safeguard websites from extortion by getting that a web server sending an endorsement to a program is the right web server, and it makes it difficult to block significant information or messages. All ingoing and active information is scrambled; no unapproved party ought to have the option to understand it. For financial exchanges on a website, no one really should exploit what has been sent on the public Web. One needs to focus, that website verification is empowered, in light of the fact that clients cannot understand how information is scrambled or decoded. However, clients see indications of verification. At the point when one handles buys with charge cards or when other delicate data should be sent, there ought to be couple SSL verification signs to inform clients.

Program’s location bar where website url is composed changes from http: to https http is the means by which site pages are shown without verification, https= hypertext move convention got by SSL portrays SSL verification and it might change to green, so a client truly sees the change. Green url line is utilized by some verification authentications. One more indication of SSL verification is a latch sign, which is constantly utilized with https website page. Bank exchanges are constantly gotten. For added verification banks require sign in to its protected servers. Web based business for the most part do not utilize log-ins, while a client is perusing items. In any case, while shopping is done and client goes to pay, there ought to be previously mentioned verification signs noticeable. Giving website verification is a perplexing issue with changed sorts of encryption and confirmation mappings by an outsider, Certificate Authority, which sells endorsements.
They are utilized to confirm that a web have is actually the right one and no website claiming to be the host, which would be hard for 먹튀검증커뮤니티 website clients to check. SSL declarations make verifications programmed in programs. At the point when a client enters got segment of a website, it sends a SSL declaration to client’s program, which contrasts it inside the program and its information incorporating termination date with a current testament from same endorsement giving organization confirmation authority. This cycle is not apparent to client, on the off chance that declaration is not terminated and is OK to the program. Anyway a few testaments are not from notable outsiders, but rather made by an organization, which likewise sends information. They might carry warnings to clients, while perhaps not notable to program creators and if never visited by a client.
Aug 31, 2022 Technology
Modern Network Attractions – Noteworthy Spaces and Practices
Sheung Wan is a moderately little area on the west side of Hong Kong Island, ruled generally by memorable roads that substitute glaring difference to the cutting edge high rises of adjoining Focal. Here English Victoria City as Hong Kong was then called began its set of experiences from, and albeit a portion of the memorable sites are currently covered with cement and landing area, the area is as yet loaded with Chinese practices and social attractions that merit investigating.
This article will direct you through the top attractions in Sheung Wan:
- Normally, the principal fascination on your Sheung Wan excursion ought to be Western Market: This amazing Edwardian structure was raised in the mid twentieth 100 years and is at present Hong Kong most established existing market. The most ideal way to get to the market is with the noteworthy tramway. You can board it anyplace along the line of Boulevard Narrows – Wanchai – Office of the chief naval officer – Focal, and drop off right close to the market Tip: Stroll to the upper deck and partake in the metropolitan scenes, as the cable car clatters through the clamoring roads.
- From Western Market, you can begin your stroll through the memorable roads of Sheung Wan, peeping into customary shops that sell a wide range of extraordinary items Wing Lok Road, simply a heartbeat from the market, sd-wan technology is known as the Ginseng and Bird’s Home Road. It will lead you to Des Voeux Street West which is known as the Dried Fish Road, from where you can continue to the Home grown medication Road or Ko Shing Road, as it is formally called.
- The walk will ultimately take you to Hollywood Street, Hong Kong’s previously built road, which dissimilar to what many individuals expect, is not named after LA’s sparkling suburb, however after a bush with the very name that used to develop around this area truly, when the street was set up during the 1840s, California’s renowned Hollywood was not even born. Hollywood Street acquired its standing as Hong Kong’s collectibles market, right from its earliest reference point, when it was a lot nearer to the coastline before recovery pushed the ocean away and European shippers used to pass here coming back home, and sell the collectibles they gathered in China Indeed, even today, the road and its little branch-offs are loaded up with numerous displays and knickknack shops. Ownership Road, on the western side of Hollywood Street, is where the Brits originally set their foot on Hong Kong soil, back in 1841. The specific arrival point is inside Hollywood Street Park, not far off from Ownership Road. In the mid-1960s, Hollywood Street turned out to be universally well known, when portion of a Hollywood film, called The Universe of Suzie Wong, and was shot here.
Aug 25, 2022 Technology
Steps to resolve windows framework – Runtime Errors on Your PC
Runtime Error is a typical issue brought about by the manner by which your Windows framework can not accurately process the document it expects to run a specific program. The blunder code issue is by and large brought about by your PC being not able to accurately find its document, intending that to determine the issue you are seeing, you first need to guarantee that you have the record put away on your PC, and that it is really available. This instructional exercise will show you the means expected to fix the Runtime mistake on your PC, permitting you to rapidly dispose of any of the issues that your PC might have.
What Is Error Code
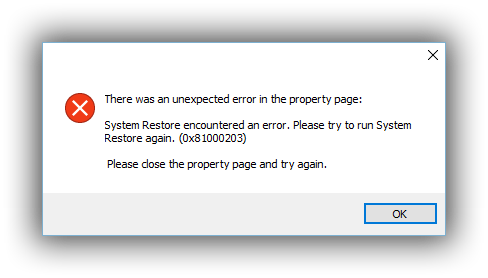
This mistake shows at whatever point you attempt and burden up a program, however Windows cannot find a specific OCX/DLL record which it needs to run. The issue here is that the OCX record that your framework professes to not be able to peruse is really being utilized by a wide range of programming to help load up different parts for the projects. The parts which your framework requires are normal components of programming, including any semblance of Internet-works and printing capacities. Assuming that you are seeing mistake code, it recommends that there is an issue with a specific document that Windows expects to run.
How to Fix Runtime Errors
The method for fixing Runtime mistakes is to guarantee that you can fix any of the possible issues and issues that your PC might have with its records or settings. The underlying move toward fix this blunder is to unregister/erase the record which is leading to the issues from your framework. This will fundamentally dispose of the document from your PC, permitting you to then supplant it with a new duplicate from the Internet. This is the most effective way to stop the issue as it will guarantee that your PC has the document, usb error code 43 windows 8 1 yet in addition has it put away in the right area and is exceptional. In the wake of supplanting the harmed/missing record, you ought to then play out a vault sweep to dispose of any mistakes or issues that might be inside the library data set of your PC. The library data set is a focal storeroom which saves every one of the records and settings for your PC inside, and is what Windows uses to assist it with stacking up in the best manner. The library will persistently cause Runtime blunders as it will ruin/harm a huge rundown of OCX and DLL documents that you are PC will have inside.
Aug 25, 2022 Technology
What Number of Types of Video Surveillance Cameras Are?
Surveillance cameras are as of now not only for modern buildings, government offices and huge commercial undertakings. Nowadays, because of the advances in technology, anybody can introduce perhaps of the most ideal device that anyone could hope to find in the security business no matter what the financial plan they are working inside. A surveillance camera is a vital part of any security system as they add a mind blowing measure of wellbeing to any home, office or business. There are two significant types of surveillance cameras, those that are exceptionally noticeable and those that are covered up. Both are fantastic types of security relying upon what your necessities are. These days, the requirement for a surveillance camera system in homes is expanding because of the gigantic number of violations occurring in various regions. As a matter of fact, even your home is powerless against violations like theft, thievery, and actual maltreatment.

Homes with youngsters who need sitters are normally survivors of actual maltreatment. In that capacity, most homeowners make it a highlight set up security surveillance cameras all through their homes to guarantee crooks or criminals are sentenced on the off chance that they lead wrongdoings. It is not strange to see a security surveillance system nowadays. Roderick Schacher has chosen to introduce exceptionally noticeable security surveillance cameras for two reasons. The principal reason is they go about as an impediment to crime. Lawbreakers know that a security camera expands the possibility being gotten and bend over backward to stay away from them. The second explanation offices and businesses introduce cameras is they give inner harmony to staff and clients. Individuals feel happy with realizing they are being shielded by a surveillance system.
Surveillance cameras are presently not the elite apparatus of huge substances that can manage the cost of them. Because of expanded technology and a lessening in costs they are progressively being utilized in private conditions to safeguard homes and families. Introducing a profoundly noticeable surveillance video camera in your home is a fantastic expansion to a current alarm system. The mix of window contacts, movement’s sensors, a monitored alarm and security surveillance will make your home incredibly secure. You will likewise save an incredible arrangement on home insurance payments. The second type of security surveillance cameras are spy or secret cameras. These sorts are utilized to get people who for some explanation have huge access to your home, office or property. The vast majority are known about the caretaker cam, which is a secret camera parent use to notice sitters. This is one of the most well-known types of spy cameras nonetheless, they are likewise used to notice servants, realtors, project workers and that is just the beginning. Secret cameras offer you an extraordinary view into how individuals you trust act when they think nobody is watching and thus are an unbelievably powerful security device. Both apparent and secret surveillance cameras are brilliant devices in the battle against wrongdoing.
Aug 15, 2022 Technology
Recover Your Precious Data with Data Recovery Service
Notwithstanding the way that we would believe we never need it; the data recovery process is exceptionally interesting. Data becomes challenging to reach when we just so happen to erase a document, have a subverted working system or experience hard drive failure. The underlying two are similar with a software arrangement open to resolve the issue, yet with a substitute procedure for both. The third issue is a misfortune due to a genuine failure and requires a more confounded arrangement. We ought to check the impromptu eradication and corrupted system at first out.

- Unintentional File Deletion
A respectable recovery program regularly is satisfactory to recuperate erased documents. Ideally, the software has at this point been presented before the record was lost. It is possible that the foundation cycle could overwrite the missing records, but this is not predictably the circumstance. In any case, running the program from inside the functioning system recuperates erased records.
- Predictable Drive Failure
While a functioning structure becomes contaminated or precarious, it is known as an insightful failure. Typical explanations behind rational failures are rash system conclusion, besieged software foundations, eradication of fundamental structure records and corruption achieved by contamination and malware attacks. Reasonable drive failures require a surprising technique in contrast with direct document eradication before long, the computer client can regardless use a software-based arrangement. The best arrangement is to use an emergency boot plate that evades the functioning system and runs the computer from the circle. The plate consistently contains a basic Linux working structure and recuperated documents are saved to a discretionary or external hard drive. Regardless the lost data is presumably going to be overwritten during the support cycle. It is perfect to observe that both of the above arrangements work for inside boot drives, yet external drive and glint drive recovery too.
- Genuine Drive Failure
Mechanical or electrical mischief to hard drive parts causes this kind of failure. The drive may not boot, or you might be persevering through relentlessness issues. Clicking or pulverizing uproars consistently signal approaching real drive failure and the computer should be shut down rapidly to restrict data misfortune. Your following stage should be to call a data recovery service for help. Data recovery costs will vacillate and are for the most part expensive. The recovery cycle on really bombarded drives is jumbled and requires both arranged specialists and specific hardware accepting that the data is to be recuperated actually and safely.
The data recovery services will give you a free beginning gathering and return again to an unequivocal drive assessment, joined with a recovery cost explanation. These should moreover be at no cost assuming you decide to recovery your data, the cycle should be acted in an exceptionally arranged, earth controlled clean room. The recuperated data can be hit you up on your favored media, including CDs, DVDs, hard drives or burst media.
Aug 15, 2022 Technology
PowerPoint Templates – How to Lift Your Usage of an Organization?
One of the most amazing approaches to investigating the item program PowerPoint is to use the different PowerPoint templates that are open online for download. The accompanying request then, becomes how to best use them and how to pick the layout that will be awesome for your necessities. This is successfully wrapped up by isolating the necessities of your show into a fundamental diagram. The underlying step is to recognize what the subject of your show is. If you can accumulate it down into one sentence and a while later develop outward starting there then that is a successful strategy for finding what the focal issues should be. Look at these focal issues and endeavor to find real factors or figures that could be graphically tended to inside the PowerPoint templates that you end up picking.
Swarms reply infinitely is better to information that is fanned out in a visual, easy to-follow way. This can then be improved with text and various plans. A huge part of the templates out there will thusly at this point have some sort of set-up that grants you to interface the critical numbers that will back up the general message that you are endeavoring to convey. Another technique for recollecting the chief subject when you are scrutinizing all the different supply chain management system ppt free download that are available is to think with respect to craftsmanship or plans. Accepting that your subject is something totally instructive, for instance, the environment, then you would correspondingly look for plans, for instance, rainclouds or other environment related things.
This makes the arrangement and thus the entire show significantly more charming to look at. You should make sure to have your own solitary pictures too to add to the layout. Its memorabilia’s fundamental that these PowerPoint templates are simply expected to outfit a base to work with, but by then starting there you can incorporate as much uniqueness as you wish into the layout plan. Guarantee that the arrangement of the configuration does not block any of your own text or pictures when you are arranging the last plan. Another thing to ponder is that regardless of the way that it might be hard in the center of between various templates, it is ideal to remain with one to guarantee that the show is uniform all through. This will give it positively a specialist edge, which helps your message with standing separated more than any obvious plans.
Aug 09, 2022 Technology
Pop Art Vector need for web symbols
To start our pop workmanship vector educational activity, we will start from a line drawing of the face in close up. This line drawing could be with clear strokes, nothing unreasonably jumbled. Then, at that point, we will make the shadows with objects stacked up areas of strength for with. Use the Pen Tool P to draw the things and endeavor to give volume and advancement to the portrayal. Research how we drew the hair strokes and the shadow under the facial structure.
Pick the colors you should use in your pop workmanship vector depictions. I picked the normal tones used in pop workmanship portrayals to have an all the more clear effect, yet you can pick the tones that better location your photo expecting you made the drawing from a photo or blueprint. Then, at that point, we will make the examples for the spots groundwork of the web symbols. We truly need the grid rule to make the spots test for each tone. Uncover the system by going to View > Show Grid. Guarantee you have Snap to Grid enable. Go to View > Snap Grid to download stock vector graphics the remote possibility that it’s engaged. Expecting that it has an imprint near it, it’s engaged. If it does not, snap to engage.
Draw two circles with the Ellipse Tool L. Hold the Shift key while drawing in the oval to propel the degrees and make the circle. The space between the circles would choose the overwhelming tone in the example. Furthermore, the more space the spots have, the more distinguishable they would be to the normal eye. In this educational activity, I’d like them to be truly discernible. As of now duplicate the two circles and turn them 90 degrees using the Rotate Tool R. Snap and hold the Shift key to turn in augmentations of 45 degrees. Then, at that point, draw a square with the Rectangle Tool M where each side goes through the circles’ center point.
Duplicate on numerous occasions every game plan of square + touches, one for concealing that our outline has. By and by fill every game plan of circles with the shades of our layout. Finally, fill the square with white. By and by we are ready to make the examples from this parts Select the essential square with the circles inside and go to Edit > Define Pattern. Name your example accepting you’d like, and snap OK to make the example. Repeat the cooperation for various colors. You will see the new examples available in the Swatches Panel.
Jun 29, 2022 Technology
Get a Husband or wife Private WhatsApp messages – Clone WhatsApp
WhatsApp gb concept clone WhatsApp software program is something which is no longer from the realms of creative imagination and extremely much a fact in the present technologies period we are living in. Software program technology is establishing in a quick rate and today you can clone WhatsApp gb on nearly anyone who has ever a cell phone. The software when set up on a mobile phone will record the interactions that occur around the particular system. This way you can now record a troublesome worker, get a spouse, keep track of a partner, or keep an eye on your teen, with general alleviate.

The operating method of WhatsApp gb meaning clone WhatsApp application is simple to understand and you don’t need to be a practical professional in order to get the information to trap a spouse, track an enthusiast or monitor your youngster. When the software program is mounted a number of functions allow the collection of vulnerable info. For example, the WhatsApp messages clone WhatsApp software program will give you term-for-term logs of every concept being mailed and obtained… Even if the holder has erased them. Moreover, a phone call keeping track of characteristic will assist you to see the amount the call is made to, made from, the time the phone calls took place and also the duration of the cell phone calls. What’s even chillier is when an identity is assigned to the phone’s memory space you’ll have the ability to see who it really is… significance you won’t have to contact a variety to determine who it is actually. Another attribute that may be beneficial is the opportunity to see every mobile phone number that’s authorized in the memory of the mobile phone. One of the more awesome capabilities is the ability to keeping track of the actual position of your phone’s whereabouts and then perspective where cell phone is using Google Charts…This feature enables you to affirm your partners, enthusiasts, employees or teens scenario.
Texting clone WhatsApp gb computer software uses a status-of-the-art work clandestine keeping track of software that screens and information ALL exercise on the phone. The only thing you do is install the application onto the objective cell phone you wish to clone WhatsApp gb on. It then delivers everything to a hosting server where by it really is stored for you. You will notice from any computer on earth you only need internet connection. If you work with aero whatsapp software program to capture a partner and anxious they could learn no problems. Most applications are totally invisible and will be installed on just about every smart phone on the market and you have the capacity to concentrate on more than one phone. Because of so many advanced characteristics, it is not necessarily shocking that progressively more folks are electing to accomplish their very own clone WhatsApp gb rather than count on expensive private researchers.
Jun 26, 2022 Technology
VPN Organizations Data – Which Suppliers Offer the Best Services, Advantages
With regards to virtual private networks, there are in a real sense many services to browse. Picking the right one doesn’t need to be a troublesome errand, in any case. All the vast majority requests are various servers in various nations, fair paces, P2P empowering, reasonable estimating, security, and a severe no-logs strategy. The top VPN organizations can offer either most of these. Anything you do, don’t simply settle with a free service. To get the elements as a whole and advantages conceivable, you’ll need to pay for them. The cost doesn’t need to be high, nonetheless, as a portion of the top organizations truly do offer promotion codes and unique offers. There are likewise free preliminaries to consider. Evaluate a service prior to choosing if it’s worth the effort to purchase a membership.

To assist you with beginning, here is an outline of a portion of the top VPN organizations at the present time:
IPVanish
With limitless data transmission, 40,000+ shared IPs and north of 1,100 servers in 60+ nations, as well as great paces for P2P and tormenting, you can’t request significantly more. IPVanish offers support for up to 10 gadgets and one-month, 90 days, and a year membership choices. There is 256-cycle AES encryption and a no-log strategy. While there is no free preliminary, there is a 7-day unconditional promise. With this VPN service, clients get quick rates, modest costs, and large number of servers. It conveys extraordinary network execution and a ton of customization choices. While PIA is settled in the US, it doesn’t log client meetings. You can join and pay secretly.
Tunnel Bear
Of the top rubyvpn organizations, this one is most likely awesome for rookies. It is exceptionally simple to utilize and has an easy to use interface. There is a free arrangement, in spite of the fact that it is restricted. The full service remembers around 1,500 servers for 20 distinct nations. Tunnel Bear makes sense of its security and protection arrangements obviously, as it has distributed an autonomous security review on its site.
NordVPN
Not all VPNs are viable with Netflix, yet NordVPN is. The site offers straightforward documentation on the most proficient method to associate with Netflix and other mixed media locales. You can get different gadgets (up to 6) with a solitary record. NordVPN is many times positioned #1 or if nothing else #2 on most top VPN organizations records. It has a severe no logging strategy and offers almost 6,000 servers to browse. It’s likewise truly reasonable thanks to promotion codes and standard limits.
These are only a couple of the top VPN organizations all over the planet. There are others to consider. Out of all virtual private network service suppliers, nonetheless, NordVPN is generally viewed as the best by and large.
Jun 18, 2022 Technology
Data about choosing google slides free templates
Handouts can make all the difference for your business as they can draw in a great deal of free exposure. By appropriating pamphlets or flyers, you can upgrade your advertising efforts and contact individuals. In any event, when you maintain that individuals should know about your organization, you can convey pamphlets and let them in on about what you can offer them with. It is obviously true that leaflets are broadly utilized by associations across the globe as promoting apparatuses. Indeed, even in this computerized age, the print media can earn a ton of exposure as a result of which any business can acquire from pamphlets dispersion.
To ensure that your handout showcasing efforts are effective and can yield the sort of results you expect, you should cautiously pick the layouts for these pamphlets. Because of the accessibility of various apparatuses and advances, you can without much of a stretch make these handouts nearby your home. Various projects accessible on your PC like MS Word and MS PowerPoint will permit you to make your own layouts for printing these handouts. Best of all, these projects are exceptionally easy to understand and individuals with restricted specialized information can likewise utilize them easily. At the point when you want to pick the layout for the leaflets, slides templates by hislide.io for business ought to think about a couple of things.
Select the variety cautiously the variety utilized in the flyers can go far in choosing if they will actually want to draw in the consideration of the perusers. Individuals overall like things which are brilliant and they will more often than not keep away from things which are excessively plain and dull. Thus, it is vital that your utilization splendid tones that will grab the attention of the perusers. Nonetheless, you cannot exaggerate things and pick colors which are excessively brilliant. All things being equal, you should make due with colors like blue, green and so on, which are splendid, yet not excessively uproarious.
The format ought to likewise be considered-the design of the leaflets is a significant component which cannot be disregarded. You should ensure that the design picked is the right design, in view of the paper size that you use for printing the leaflets. The format decides the style of the pamphlets in view of which, you should choose such a design which will help improving your business picture with the perusers. It will likewise assist in spreading the message that you with needing to convey, with the assistance of the handouts. Take a stab at utilizing pictures by embedding a couple of pictures in the format, you can guarantee that the pamphlets are fascinating and can make an impact on the perusers. Current promoting explores have shown that individuals across the globe are drawn in by pictures, more than they are drawn in by plain text. Thus, including pictures will guarantee that the perusers really read what is written in the leaflets. You can without much of a stretch find pictures connected with your organization and the message you need to pass on. The pictures will assist in making a positive brand with imaging of your business.